This is a quick guide showing how to configure Episerver to use Active Directory instead of Multiplexing/WindowsProvider. This is NOT showing how to use Azure AD.
Im testing this on a new Alloy site running Episerver 11.3.1.
NOTE, while this is a quick way of adding Active Directory support, I still recommend using ADFS or something similar instead.
Some good resources if you want to read more about this topic:
- Configuring Active Directory membership provider - Episerver.
- Mixed mode authentication - Mark Hall
- Episerver with Axure AD authentication - Nicola Ayan
Active Directory
My AD setup.
- Domain:
local.josef.guru - AD Service account:
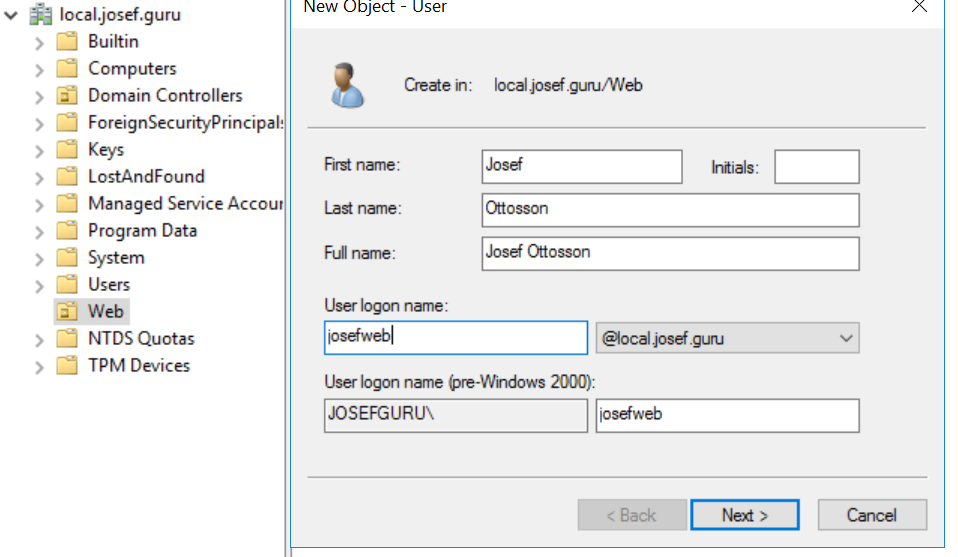
service@local.josef.guru, this is a normal user account responsible for connecting to the AD, used in the Membership/RoleProvider section inWeb.config. - AD user in correct OU. In my case I will name my user
josefweband the OU will beWeb - AD Groups named
CmsAdminsandCmsEditors(you can name these groups whatever you want).
Here's an image of how my AD is setup, it's pretty standard, for this guide I've added a new OU(Organizational Units) named Web where I will add all users who will be able to access the Edit interface.
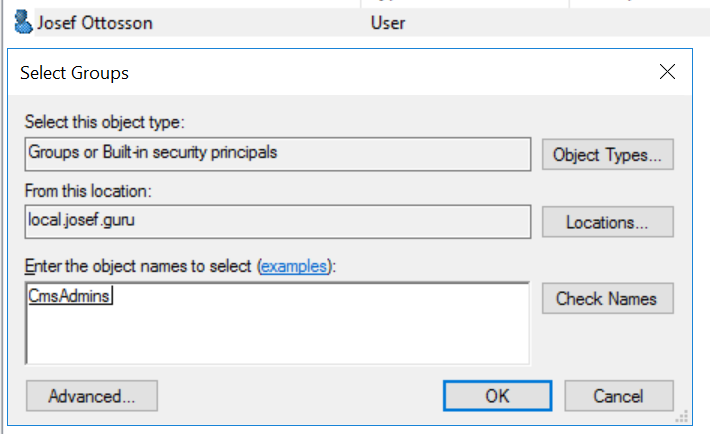
The users also needs to be a member of the correct groups to be able to login. I will add my user to the group CmsAdmins which means that this user will be able to do everything in the cms/admin(because we will map this role to the virtual role CmsAdmins further down).
Web.Config
Membership/roleprovider
Change the <membership> section to the following
<membership defaultProvider="ActiveDirectoryMembershipProvider" userIsOnlineTimeWindow="10" hashAlgorithmType="HMACSHA512">
<providers>
<clear />
<add name="ActiveDirectoryMembershipProvider"
type="System.Web.Security.ActiveDirectoryMembershipProvider, System.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="ActiveDirectoryProviderConnection"
connectionUsername="service@local.josef.guru"
connectionPassword="mypassword"
enableSearchMethods="true"
attributeMapUsername="sAMAccountName" />
</providers>
</membership>
Change the <rolemanager> section to the following
<roleManager enabled="true" defaultProvider="ActiveDirectoryRoleProvider" cacheRolesInCookie="true">
<providers>
<clear />
<add name="ActiveDirectoryRoleProvider"
type="EPiServer.Security.ActiveDirectoryRoleProvider, EPiServer.Cms.AspNet, Version=11.3.1.0, Culture=neutral, PublicKeyToken=8fe83dea738b45b7"
connectionStringName="ActiveDirectoryProviderConnection"
connectionUsername="service@local.josef.guru"
connectionPassword="mypassword"
attributeMapUsername="sAMAccountName" />
</providers>
</roleManager>
Connectionstring
Add a new connectionstring, ActiveDirectoryProviderConnection
<connectionStrings>
<add name="ActiveDirectoryProviderConnection" connectionString="LDAP://local.josef.guru/OU=Web,DC=local,DC=josef,DC=guru" />
....
</connectionStrings>
If you are unsure about how your LDAP connectionstring should look, read this.
Virtual roles
Map the virtual roles, we want to map our AD groups CmsAdmins/CmsEditors to the virtual roles CmsAdmins and CmsEditors, this is achieved by populating the roles attribute. I've also removed the default WebAdmins, WebEditors and Administrators roles.
<virtualRoles addClaims="true">
<providers>
...
<add name="CmsAdmins" type="EPiServer.Security.MappedRole, EPiServer.Framework" roles="CmsAdmins" mode="Any" />
<add name="CmsEditors" type="EPiServer.Security.MappedRole, EPiServer.Framework" roles="CmsAdmins, CmsEditors" mode="Any" />
...
</providers>
</virtualRoles>
Location sections
You will need to edit the authorization section under the following locations:
- EPiServer
- EPiServer/CMS/admin
It should look like this <allow roles="CmsAdmins, CmsEditors" />
Example:
<location path="EPiServer">
<system.web>
...
<authorization>
<allow roles="CmsAdmins, CmsEditors" />
<deny users="*" />
</authorization>
...
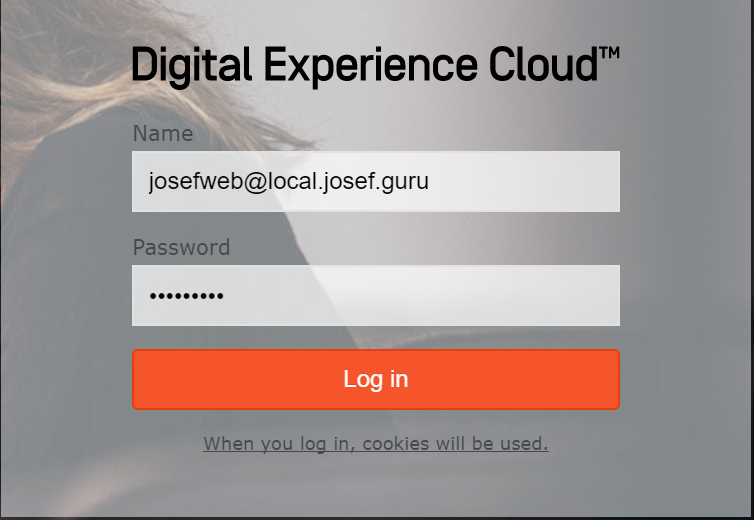
You should now be able to login!